The dark web is a hidden, unregulated frontier in the vast expanse of the internet. Want to know if your personal information is being sold on the Dark Web? In this blog post, we’ll explore free methods to check if your data is part of any data breach and exposed on the dark web.
What Is the Dark Web?
The Dark Web is a hidden part of the internet inaccessible through regular web browsers or search engines. Hackers, criminals, and other shady actors often use it to trade and sell stolen information, illegal goods, and services. To access the Dark Web, you need a special browser, like Tor, that encrypts your data and hides your identity.
How Do I Check if My Data Is Exposed to a Data Breach?
A data breach is when a hacker breaks into databases containing your personal information like name, email, password, credit card, or social security number and leaks or steals this data. This information can be used for malicious purposes like theft, fraud, or other crimes.
Method 1 – Aura Dark Web Scan
Aura offers free Dark Web scans to check if your personal information has been leaked in a recent data breach. Aura scans your email address among the depository of compromised credential databases and alerts you if it finds a match. You can also sign up for Aura’s identity theft protection service, which monitors your credit reports, bank accounts, social media accounts, and more for signs of identity theft and helps you restore your identity if required.
To run a free Dark Web scan with Aura, follow these steps:
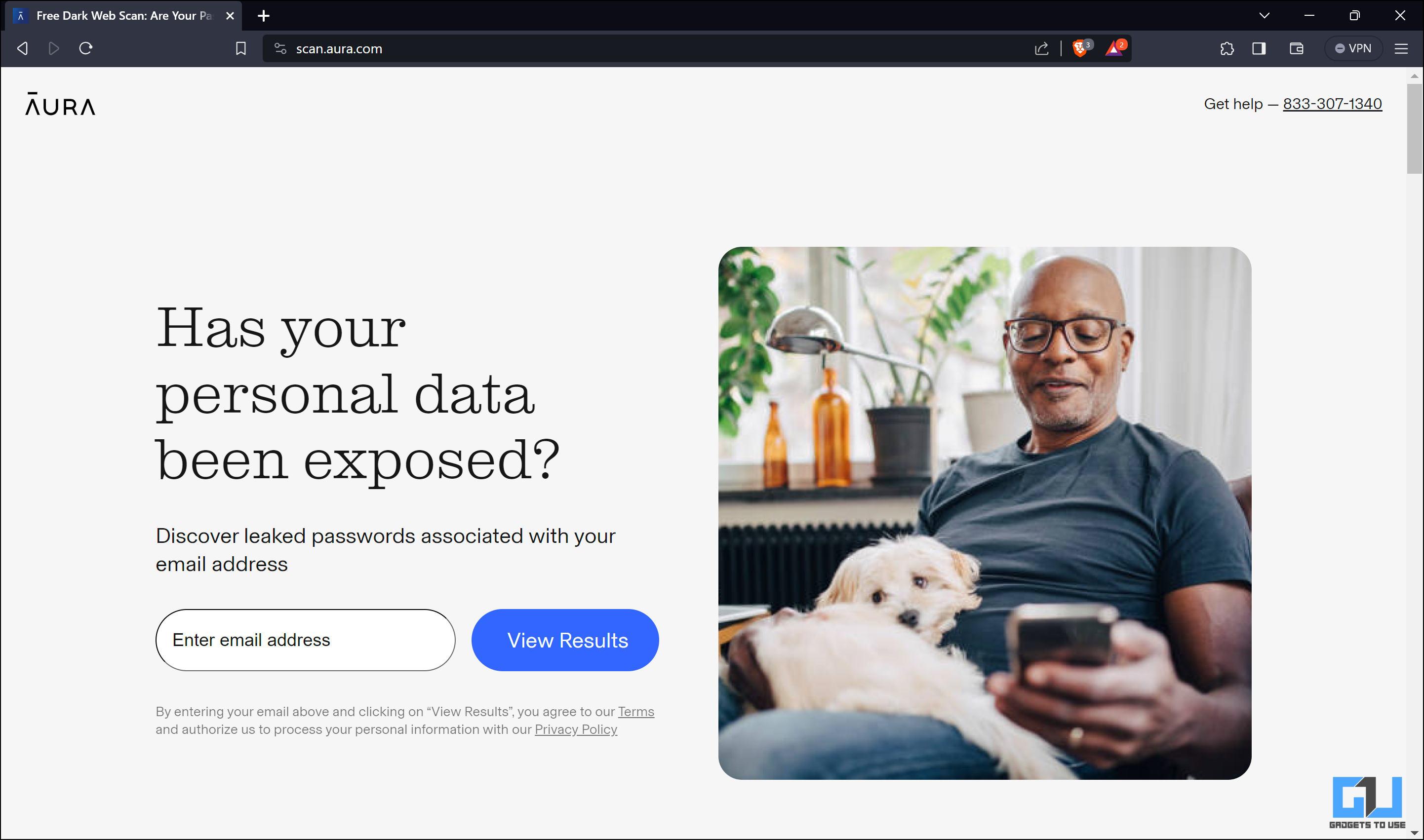
1. Go to the Aura Free Scan page on a web browser.
2. Enter your email address and click View Results.
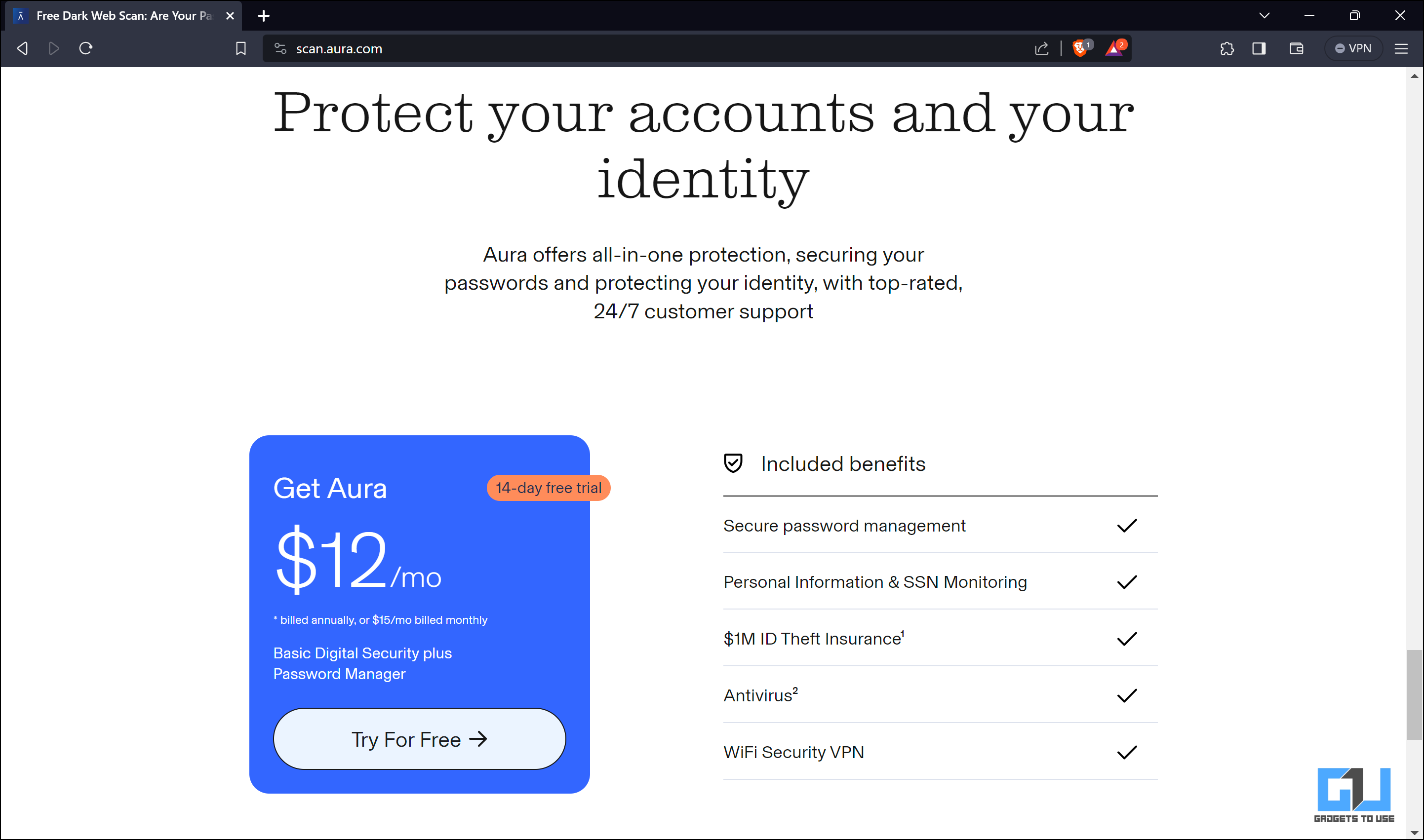
Aura will scan your email address with the compromised credential databases and show you if it finds any breaches. When your details match with a leak, it will inform you about the compromised source. To check for such breach, you must opt for a $12/month subscription.
Method 2 – Google Password Checkup
Google Password Checkup is a feature that helps you check if any saved passwords have been compromised in a data breach. Google Password Checkup works with Chrome browsers and Google accounts. It compares your passwords with a list of over four billion leaked passwords and warns if any are unsafe. You must change your passwords to protect your accounts.
To use Google Password Checkup, follow these steps:
1. Open the Chrome browser and sign in to your Google account.
2. Go to the Google Password Manager page and click Go to Password Checkup.
3. Now click Check Passwords and enter your password to initiate checkup.
4. Google will search for your password in the leaked database and let you know if there’s a match.
Method 3 – Use Google One Dark Web Report
Google One Dark Web Report lets you check if any of your personal information was part of a data breach and exposed on the Dark Web. It is limited to Google One members, bundled with cloud storage, phone backup, and other benefits. Google Dark Web Report monitors your email address and phone number for signs of exposure on the Dark Web and sends you alerts if it finds any matches.
To use Google One Dark Web Report, follow these steps:
1. Sign up for a Google One membership.
2. Go to the Google One home page and click the Dark Web Report Setup Option.
2. Click on Start Monitoring.
3. On the next page, select the additional info for the report and click Allow.
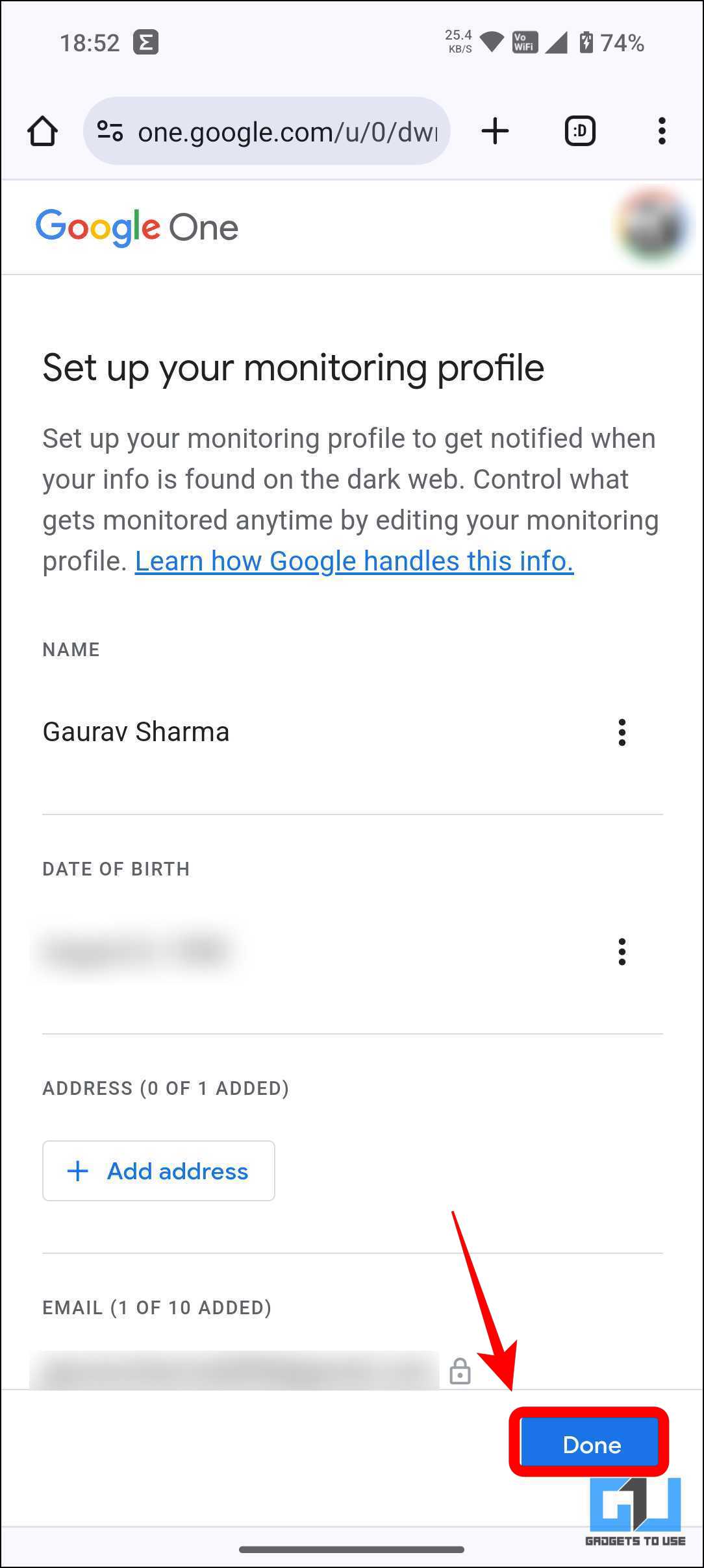
4. Set up your monitoring profile by editing and adding the essential info, then click Done.
5. Google scans your data on the dark web and reports if any of your data is exposed.
Method 4 – IDStrong Dark Web Scan
IDStrong is another tool to scan for data breaches and alerts you if any match is found on the dark web. It scans your email address, phone number, Social Security number, driver’s license number, passport number, medical ID number, bank account number, credit card number, and more.
To run a free Dark Web scan with IDStrong, follow these steps:
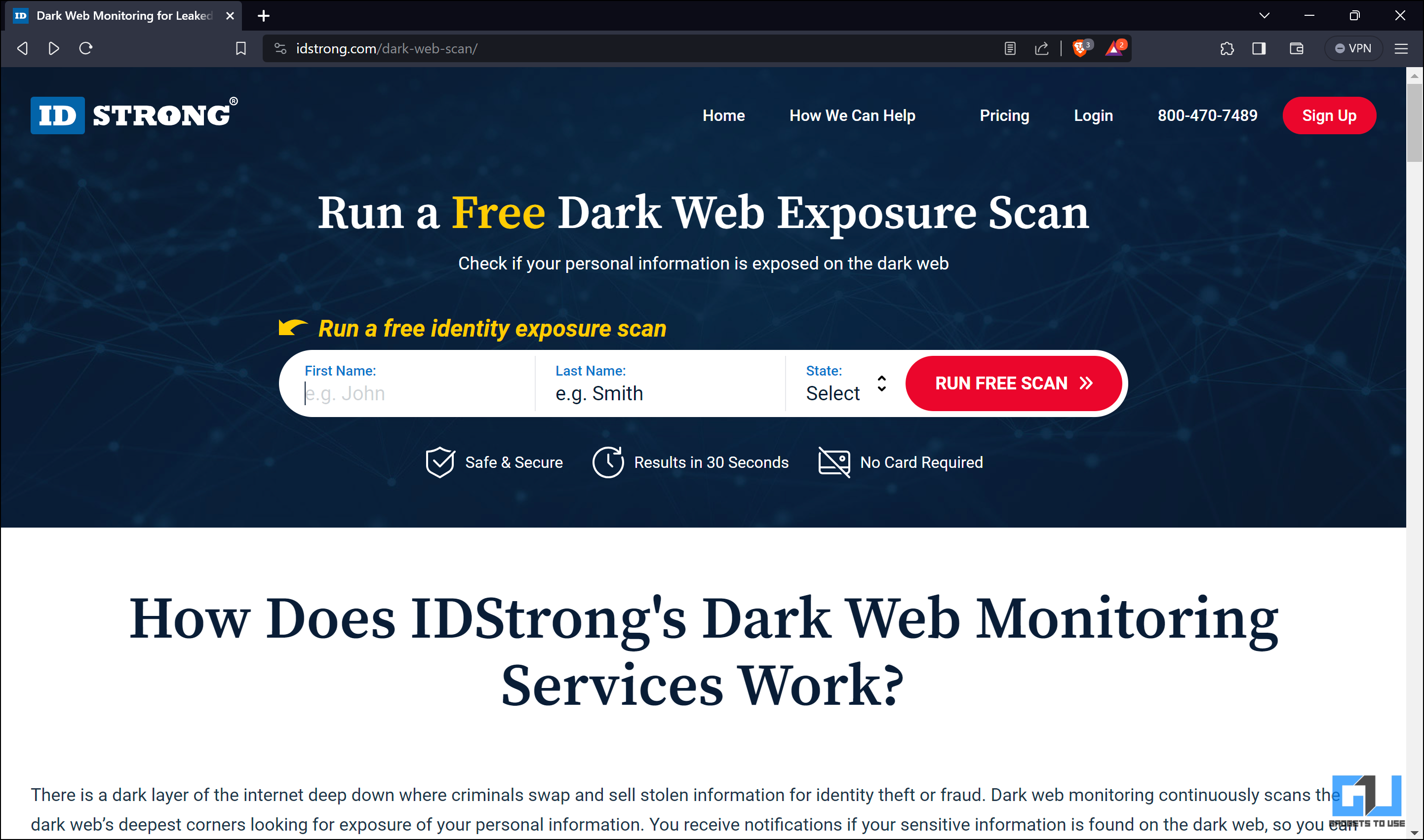
1. Go to the IDStrong Free Scan page to enter your details, like first and last name and state, and press Run Free Scan.
This will provide a list of possible matches. Find your name and click on Continue Scan.
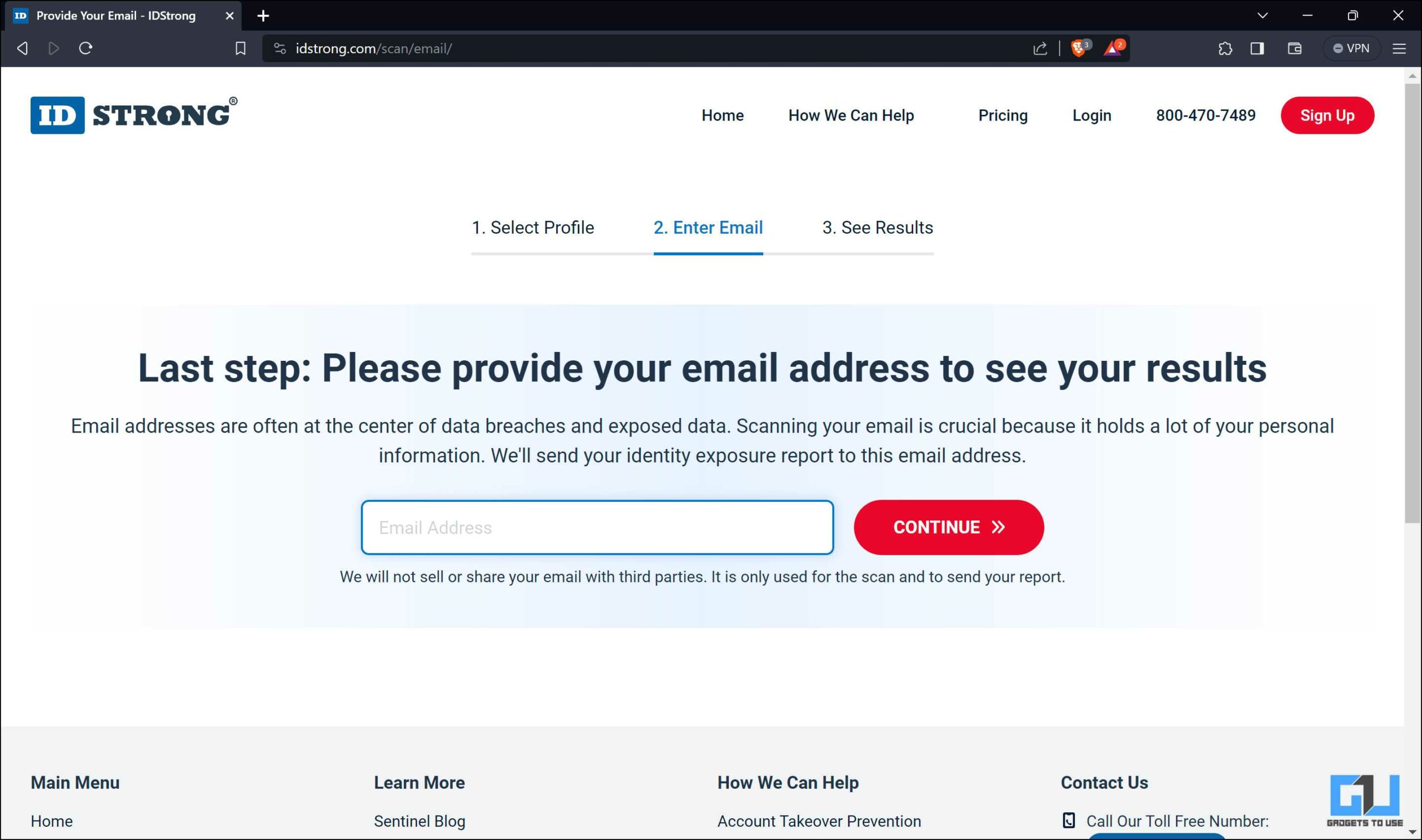
2. Enter your email address and click Continue.
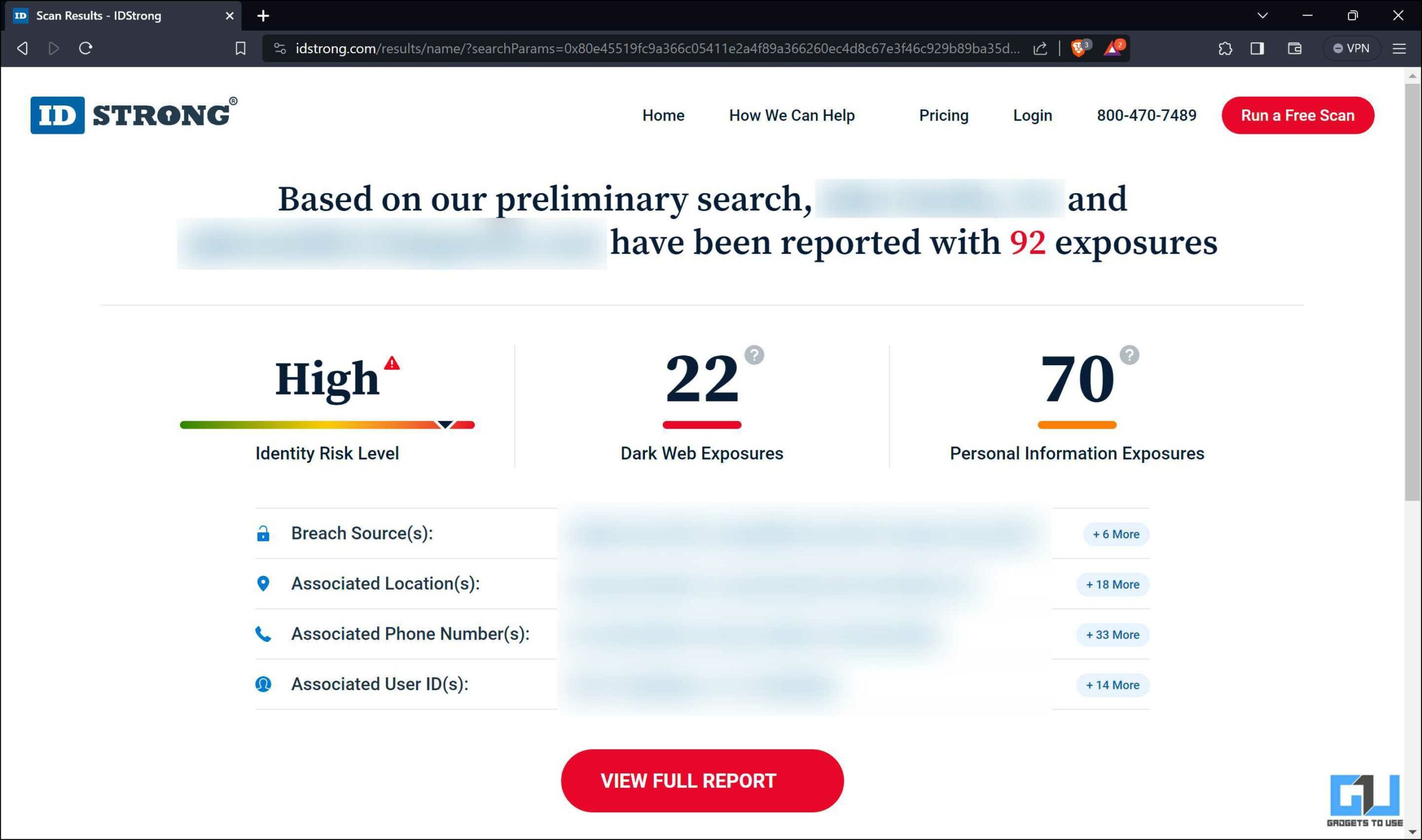
3. IDStrong will scan your email address with the compromised credential databases and show you if it finds any matches.
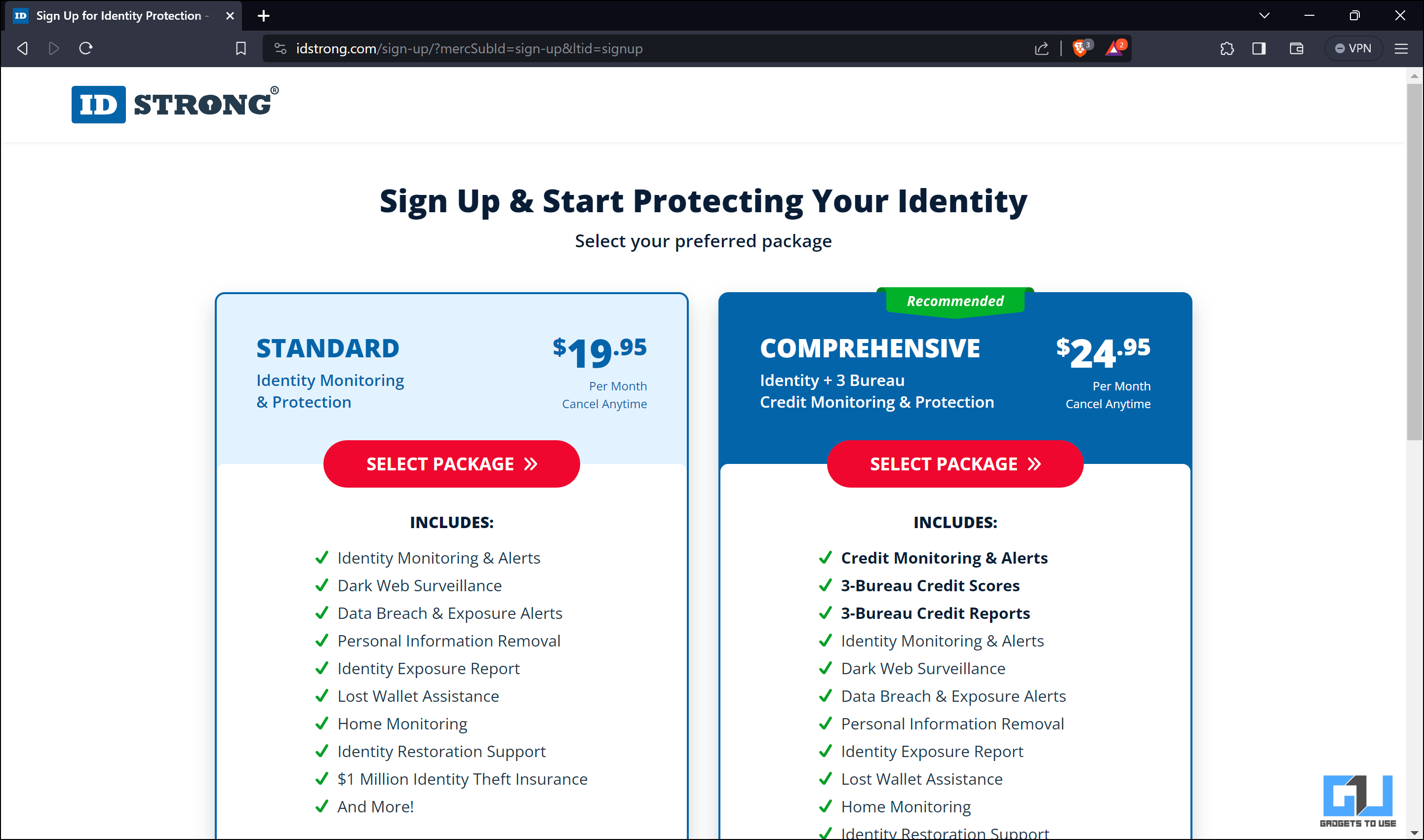
4. To get the full report, you must pay a small amount or opt for a subscription that includes regular monitoring and alerts.
You can also sign up for IDStrong’s identity theft protection service, which monitors your credit reports, public records, court records, and more for signs of identity theft and helps you restore your identity. However, as of now, this is for US citizens exclusively.
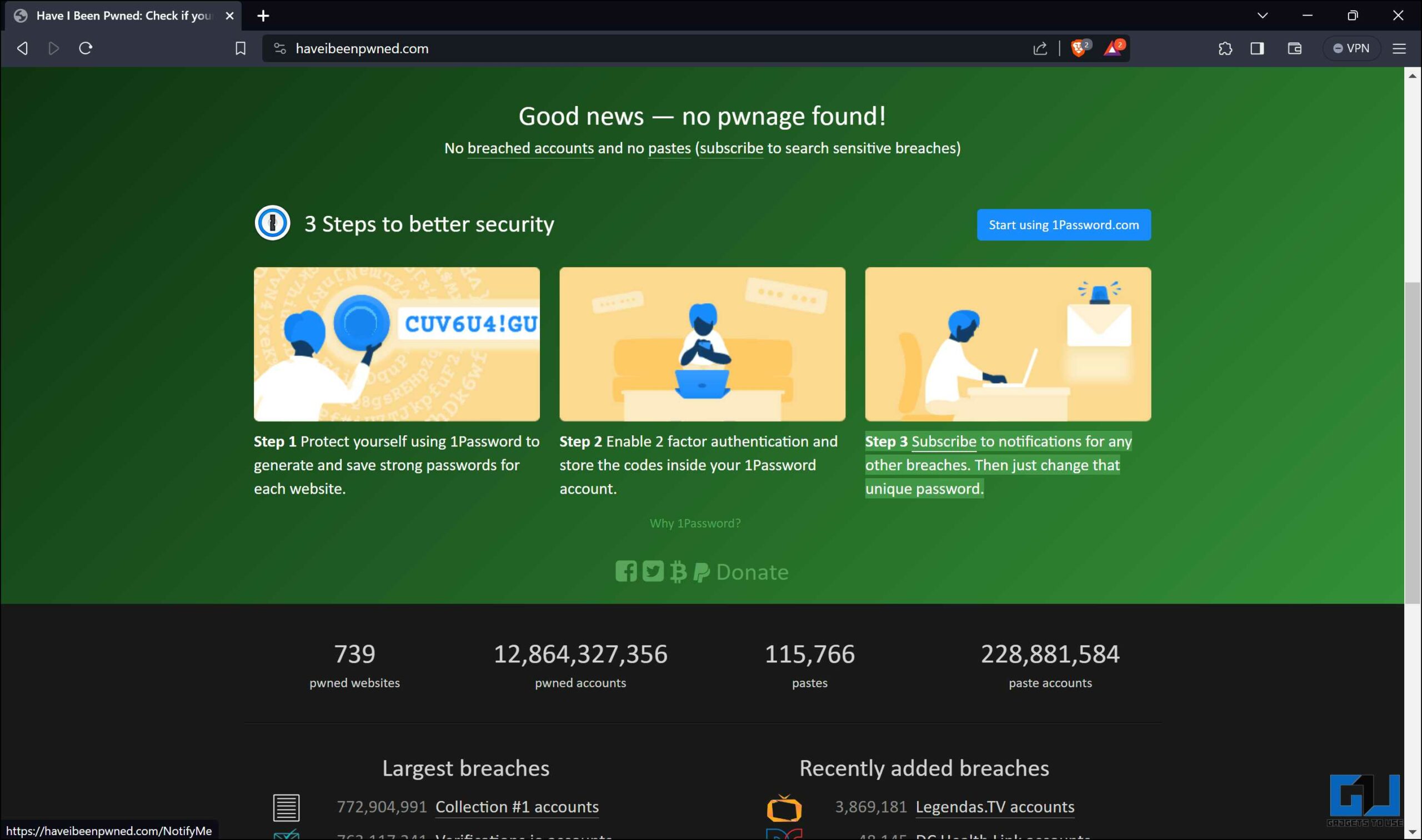
Method 5 – Use Have I Been Pwned?
Have I Been Pwned analyzes a vast collection of breaches and warns you if your data has been leaked. You can also sign up for its notification service, which alerts you if your information appears in a new data breach.
1. Visit the Have I Been Pwned website, enter your email address, and click “pwned?.”
2. The service checks for your information with the compromised data in breaches and shows you the specifics.
FAQs
Q. What Is a Data Breach?
When a hacker breaks into the databases of websites, apps, or organizations that store your data, leaking or stealing your personal information, such as your name, email, password, credit card number, or Social Security number.
Q. How Do I Check Whether My Information is on the Dark Web?
Check the five tools mentioned above to protect your data from dark web leaks.
Q. Is the Google Dark Web Report Free?
No, the Google Dark Web Report is not free. It is a bundled feature and part of the Google One membership, a subscription service that costs $1.99 per month for 100 GB of cloud storage and other benefits.
Q. Can I Remove My Information From the Dark Web?
Removing your information from the Dark Web is not easy. You can change your passwords, enable two-factor authentication, freeze your credit reports, and monitor your accounts for suspicious activity. You can also use an identity theft protection service like Aura or IDStrong to help you prevent and recover from identity theft.
Wrapping Up
If your personal information ends up on the Dark Web after a data breach, you could become a target for identity theft, fraud, or other malicious activities. The dark web can be daunting, but you can protect your personal information with the right tools. The five methods we’ve discussed provide a starting point for you to take control of your digital footprint. Remember, vigilance and proactive measures are your best defense against data breaches. Stay tuned to GadgetsToUse for more such reads, and take the necessary steps to secure your personal information.
Also, Read:
- Top 9 Privacy Apps to Use: Prevent Tracking, Block Ads, Data Collection
- Top 9 Security Tips to Use Paytm Safely in 2023
- 16 Best Privacy Tips for Telegram (2023)
- 6 Privacy Features of Windows 11 You Should Use Right Now
You can also follow us for instant tech news at Google News or for tips and tricks, smartphones & gadgets reviews, join the GadgetsToUse Telegram Group, or subscribe to the GadgetsToUse Youtube Channel for the latest review videos.